Article Updated: 14 July 2019
According to our source, this problem was caused by ElephantData SDK (dev toolkit which provides ads monetization, market intelligence and analytics). Many developers are, apparently, offered to use their SDK under lucrative conditions, but it seems to contain a malware, even in the latest available version (2.3.7). If this is true, both users and developers are in danger unless they remove the offending SDK or it gets fixed.
This is the only relevant page we discovered that potentially discusses security of their SDK implementation (Stack Overflow in Russian). And another good read for app developers.
We are not sure if they are aware of this or not, we will try and contact them for a comment and report back here with their response. Update: After 45 days we still haven’t received a response.
This seems to be a second major incident with Android OS and Google Play Store in recent months. Another one was with a company behind famous ES File Explorer app.
ScreenStream Mirroring Free app was triggering the browser hijack — in my case at least, there are probably many other infected apps out there! Be sure to watch out and report them at Google Play Store.
> Developer promptly responded to our report with reply that this was most definitely not intentional, updated their app and fixed the issue.
How To Report An App on Google Play Store?
- Run Google Play Store app on your device
- Find (use Search icon) and open the offending App’s page
- Click on 3-dots menu in the top right corner and choose Flag as inappropriate option
- Pick Harmful to device or data option and enter brief summary of what you discovered
Latest updates:
- Avast does not fully help as initially believed
- VirusTotal app for Android Mobile added to scanning tools list (didn’t help fixing this)
- Team from Kaspersky Lab created special debugging app (unofficial for now) that acts like a browser in order to catch rogue app – UPDATE: Intent Catcher app didn’t help!
- Team from Kaspersky Lab created special Firefox browser with all action logging capability – it is working!
- With so many unrelated, completely different apps being reported (e.g. ScreenStream Mirroring, Opera Mini, Pi Music Player etc.), there must be a common denominator here, like an infected Ad Network SDK exploit, commonly used dev-kit component or something related.
The Journey Begins
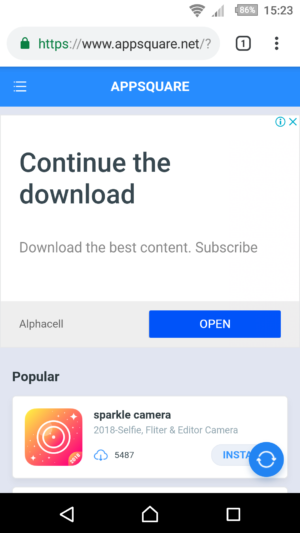
Recently, literally out of the blue, my Android phone started acting very strange, all by it’s own free will occasionally starting Chrome browser app and automatically opening appsquare.net (go on click on it – our link just opens google search results – not actual malware page) website filled with advertisement. Searching the web, turns out it was related / connected to novelcamp.net malware.
There was no apparent rule what triggered this behavior, was it some app, some random event, and it even occurred right after clean phone restarts couple of times. Google Play Store’s Play Protect service did not find anything suspicious on initial scan, and initial Google search didn’t help, either.
Only changes done recently were installed few very popular games from Play Store, couple of them removed in the meantime, and no 3rd party apps from unknown or independent publishing platforms were installed. Phone was clean and used mostly for work. No suspicious websites were ever visited on this device, so the chance of catching up something with implied risk was out of the question. Just a regular, ordinary use, really.
Is there an easy solution to fix this?
How To Fix AppSquare.net / NovelCamp.net Malware – Browser Hijack
I tested couple of free anti-malware apps from Play Store (all of them are ad-supported, but that’s OK) and here are my findings.
AVG AntiVirus for Android
We start our journey with a well-known AVG protection tool back from the days when desktop PCs powered by Windows operating system were extremely dominant home-computing platform, and mobile segment was dominated by various dumb and Nokia’s Symbian smart phones. Those were the days…
Unfortunately, at the time I was infected by this pest, latest AVG Free Edition version was not able to fix it. In fact, it still happened regardless of AVG app being installed and full scan performed.
Malwarebytes AntiMalware for Android
Our next trial was a solution from Malwarebytes – almost equally known protection app as above AVG, but, apparently, much less popular on Android according to official Google PlayStore stats, which also turned up on first page in Google Search results for NovelCamp infection.
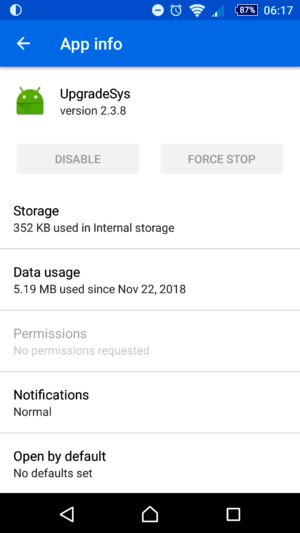
After performing device scan, Malwarebytes tool reported usual check points e.g. unprotected WiFi network, enabled developer USB debugging mode that should be turned off, and one thing AVG was silent about: UpgradeSys system app with known vulnerabilities and attack vectors.
Well, I just briefly stopped the app, as it is not possible to uninstall it directly from the Apps without root access (check Malwarebyte’s website for instructions how to do this on non-rooted phones if you are interested), but later, with each phone reboot (restart) it was up and running again.
However, somehow I was still not convinced that this was the problem, and decided to move on to the next available app and hope it will fix the problem, which was still happening, btw!
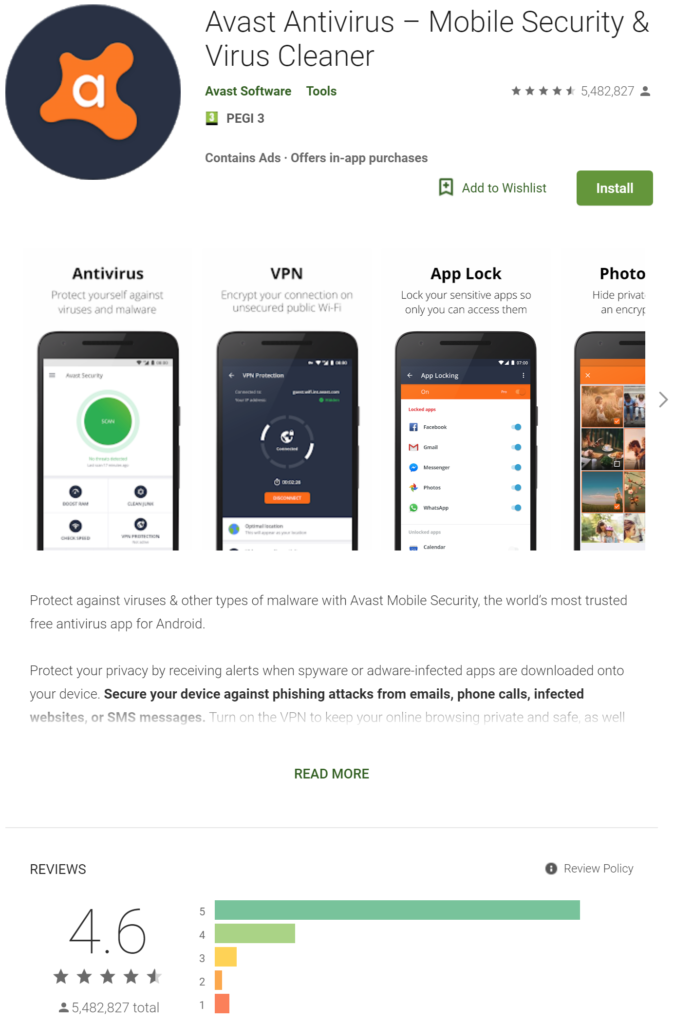
Avast Android Mobile Security
One of my final hopes was to try Avast for Android. I used it occasionally on some of my PCs, particularly those used by relatives, as they frequently end-up with malware infections eventually. Avast just postpones that process a lot longer, if not entirely prevents it.
Anyway, once installed, Avast also offered an option to activate Advanced Web Shield continuous protection. I said – what the heck, nothing to lose here, so full browser monitoring was active. Yes, that probably invades your privacy, as Avast will scan all the visited URLs regularly in the background, but I had to catch the culprit and get rid of it.
Minor annoying thing is that Avast constantly displays message in your notification area “We’re always protecting you” or something along that line. At first, you might think this is some marketing crap or whatever, but if you visit Avast Settings later and wish to turn it off, you will learn that by disabling this notification you may jeopardize Avast continuous protection, as Android may kill the background app to preserve system resources and battery. Alternatively, you can replace it and select other optional appearances in form of a quick access and control toolbar / curtain widget.
After initial full scan and few issues ‘fixed’ in the Activity Log (there is no way to tell what they were, unfortunately), 3 days have passed and there was not a single occurrence of annoying random Chrome app launch with appsquare.net homepage opening. Hooray!
After 3 days of continuous running, as an experiment and proof test, I decided to uninstall / remove Avast (or avast!) completely and see if the pest was just quarantined or actually fixed.
7 days later, at the moment I am writing this, still nothing. There is nothing else I can do, except to draw a conclusion that it was – fixed.
ANDROID MALWARE BROWSER HIJACK RETURNS
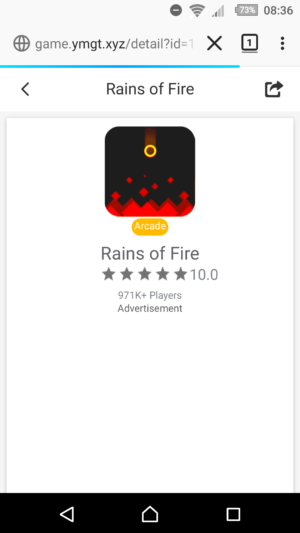
UPDATE: Unfortunately, the issue returned. This time, instead of appsquare.net, the domains (websites) were new.qwer1234.xyz and game.ygmt.xyz. Obviously, generic domains (with subdomains) full of advertisements. Ads are also served by Google Ads and since all websites pass human stuff screening tests before actual approval to be able to serve ads by Google, this only means that this is a very carefully designed malware campaign.
Avast was installed again, with advanced shield and storage scanning turned-on. Remains to be seen what will happen next. However, it happened again even with Avast’s persistent advanced shield being active.
It seems that this malware is exploiting vulnerability in ad serving network to execute a scheduled browser hijacking event. Google warned about BatMobi Ad SDK in December, and already pulled several apps from Play Store since. At this moment no true solution exists, except to locate the apps which use unreliable ad networks and exploits.
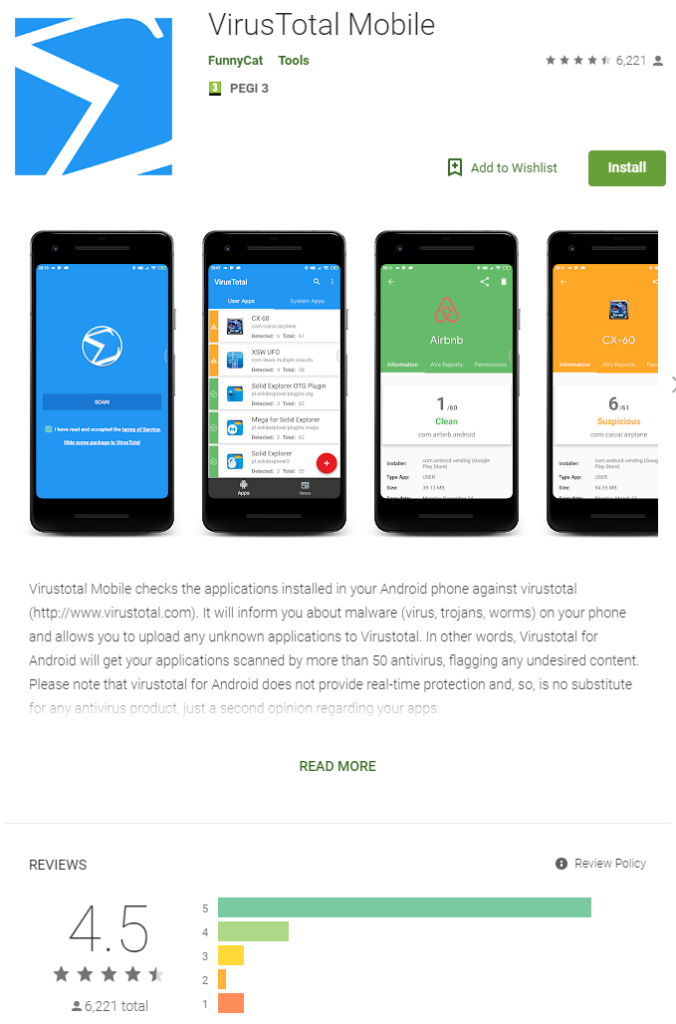
VirusTotal for Android Mobile
VirusTotal is a famous free anti-malware / anti-virus file scanning online service now owned by Google (Alphabet Chronicle). Whenever you are suspicious about certain file you wish to download (or already downloaded) from internet, you can use URL or FILE upload tool to scan it.
VirusTotal runs virtual machines in the background with various malware detection tools and returns a score / detection message if anything is found. Be aware that sometimes there could be a false positive, which is usually manifested by high negative/positive ration from many tools. On the other hand, sometimes only a handful of tools can detect certain new form of attack, before others get updated, so you should be careful in all cases.
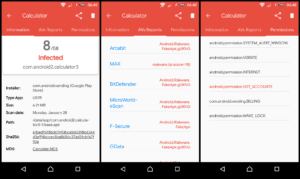
I downloaded mobile version of VirusTotal (app is officially listed on VirusTotal website), and scanned all installed apps. Tool found only one app with the problem, an ad-free Calculator. Because, this calculator is ad-free (it does not display any ads, and has in-app purchase upgrade), I doubt it is the one responsible, since I have it installed for at least a full year now.
I have removed this app. However, low detection ratio 8/58 can mean a false positive here.
If ad-serving network is compromised, it may not be detected easily and right away, if the exploit does not itself contain anything dangerous, and just executes on a scheduled / random basis and then removes all the traces as evidence. Waiting game is still ON.
KASPERSKY LAB – Browser Hijack Detection Apps
Team from Kaspersky Lab put considerable effort with special apps that can pose as a default browser and try to catch the application that triggers browser hijacking events.
Forum topic (in Russian):
https://forum.kaspersky.com/index.php?/topic/409072/
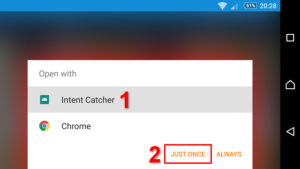
Intent Catcher App
UPDATE:
Intent Catcher app didn’t help! Popup happened again apparently bypassing browser selection dialog.
It might help if you set this app as default browser to open all supported links without android’s app selection / confirmation dialog — haven’t tried this because I switched to modified Firefox app in the meantime — read further section below.
Intent Catcher App – Demo Video:
https://box.kaspersky.com/f/ca86500e9654426385f0/
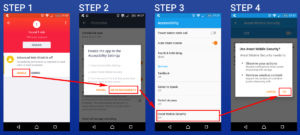
Quick Instructions:
- Download Intent Catcher .APK file
- Install .APK file (you must enable apps from unknown sources temporarily)
- Disable DEFAULT BROWSER option in your Chrome, Firefox or whatever app you use:
Android Settings > Apps > APP NAME > Open by default > Clear All Defaults - App will kick-in for all http links that are automatically triggered and you have to select JUST ONCE / This Time Only option (alternatively, you can set it as a default browser app right away, because recommended method didn’t work in my case and hijacked Chrome session was automatically started again bypassing Intent Catcher completely!)
- App will report to you which app did it
- Uninstall or disable reported app and wait for an update
Firefox Browser App – Special Activity Logging Build
UPDATE:
After Intent Catcher initial failure, Kaspersky Team’s second attempt was a special Firefox app browser build that logs all activities.
Quick Instructions:
- Download Custom Firefox .APK file from your phone
- Install .APK file (you must enable apps from unknown sources temporarily)
- Start Custom Firefox browser and set it as default temporarily until you catch infected app
Android Settings > Apps > (custom) Firefox > Open by default > Open supported links and set Open in this app option
- App will kick-in for all http links that are automatically triggered
- You must manually grant WRITE ACCESS for logging activity:
Android Settings > Apps > (custom) Firefox > Permissions and enable Storage permission
- The application will log all activity in /internal storage/moz_url_log.txt file
- Uninstall or disable reported suspicious app when appsquare/novelcamp page pops-up and wait for an update
UPDATE:
Kaspersky Firefox browser special edition app is working! It caught our infected app!
How intercepted hijack session looks:
Content of moz_url_log.txt:
WHAT HAVE I LEARNED FROM THIS SECURITY INCIDENT ?
I consider myself educated technology person, which does not mean that attribute can protect me from all the dangers that are lurking around the modern web.
And I can usually tell the difference between a fake advertisement and true / valid ad banner, malicious URLs (web links) and DOs and DONTs of internet usage. However, even to the best of us this kind of infections can sometimes happen.
Apparently, we are already living in an era when using your smart phones without some 3rd party protection is like walking almost completely naked on the street, despite effort from Google with Play Protect and multiple layers of app screening tests.
Disturbing fact is that neither Play Protect nor any available Anti-Malware / Anti-Virus apps discovered that something was wrong. Even with full browser protection and monitoring option active.
Just recent Play Store apps incidents (read more about this on links listed below), which revealed some extremely popular apps and games being infected with initially undetected malware until millions of users already installed and heavily used them, is alarming trend, to say at least.
You have to stay safe using all available means, of course, within some common sense boundaries and safety rules, because modern smart phones are not just phones, they are paying gateways and personal IDs.
Developers have a huge responsibility – now more than ever. Including 3rd party SDKs is a huge risk both for their and users security, particularly those from closed unknown sources and alike, under suspiciously beneficial conditions (when money is involved). Developers risk that their apps or accounts get banned/closed, and users get exposed to unwanted spam, data collection and even personal data leaks. The scariest part in all this is the fact that end users are completely unaware and out of control!
Always remember that even the best state-of-the-art anti-virus and anti-malware software can only protect you from a known threats, and not new and unknown exploits and vulnerabilities. False sense of security is more dangerous than no security at all, figuratively speaking. Even account protections can be bypassed, as history has demonstrated on multiple occasions.
We thank Kaspersky Team for helping us solve this issue!
External Related Resources
https://security.googleblog.com/2018/12/tackling-ads-abuse-in-apps-and-sdks.html
https://www.reddit.com/r/GalaxyS9/comments/ai98c0/novelcampnet_automatically_pops_up_in_android/
https://piunikaweb.com/2019/02/23/our-analysis-on-annoying-chrome-ad-popups-on-samsung-phones/










![Xiaomi App - How To Re-Install Stock Factory Version - How To Fix Corrupted Gallery App [no root]](https://tehnoblog.org/wp-content/uploads/2025/09/Xiaomi-Gallery-App-Code-Bugs-Artwork-1024x576.png)















41 Comments
Add Your CommentCan I email you- having the exact same issues. Not very tech savy- getting a little lost once I downloaded Firefox. Thanks
April 1st, 2019Hi Tony, after you downloaded and installed Firefox app, you are already half-through. All you need to do now is make Firefox your default browser app.
EASY WAY
Open Firefox app that you just installed, look at the top right corner and see 3 vertical dots (drawer menu icon). Tap on it, and scroll all the way down near the end and click on option named Make default browser.
MANUAL WAY
Go to Android Settings, then Apps, and there you will have the list of all installed apps. Once you locate Firefox, just click on it to open info/options, and as instructed in the article, set it as default app for supported links. Then just wait for hijack event to happen.
* * *
In the meantime, if you use Gmail or some other email app, you can try opening any link in some emails, just to verify that Firefox is default browser and it is working. Alternatively, if you use WhatsApp, Viber or some other messenger app, you can send to you or some friend a simple link text, e.g. just type-in google.com and send a message. Then, click on that link and it should be opened by Firefox.
If that’s not the case, you will be presented with a pop-up dialog to select an appropriate app for this action e.g. Chrome or Firefox, and you have to select Firefox and make it default (pick Always option). Don’t worry, later when you remove Firefox app, Chrome will be again your default browser, or you may continue with Firefox, that’s up to you, really.
* * *
After hijack event occurs, you need to locate Firefox’s app log file, and for that you need a File Manager or File Explorer app. You can use Google’s Files app for that, open Files app, tap on Browse button (look at the bottom in the middle of your screen) and select Internal Memory. Log file is usually in the root (main, top) folder of your internal phone memory / storage, as mentioned in the article.
It is really simple, just follow it step by step.
April 1st, 2019Hey, I can’t seem to find the log file.
June 22nd, 2020Hi everyone!
Thanks for your support.
I have the same problem with YMGT Games pop up Adware , in this case … The malicious app is com.impactobtl.friendstrackerfree.com an app that i use to see how delete me in Facebook xD but now I deleted it.
Thanks for all.
June 23rd, 2019Had the same problem, caught the log file on Files app. Now I’m not sure if I’m doing this right:
I opened the file, my phone asked with what app. I chose docs. The text on the doc is following: com.guruinfomedia.gps.speedometer : http: // c.nicedll.com/scene/ (utm portion redacted)
So basically looks like guruinfomedias speedometer app was the culprit? I deleted it, and now have to see if it was the real reason. Text above was written a week ago.
Apparently I hadn’t posted this comment. Deleting Speedometer solved the problem for me.
June 27th, 2019Is it possible to inform Play Store about the malware?
Hi Laura, that URL seems to open advertisement page, so the app looks like definitely infected. You can report any app in Play Store as described in the beginning of this article. Thanks!
June 28th, 2019I have followed all the steps but there is only one problem. I cannot change the supported links option. I can see it in open by default but I can’t select it. I’m not sure how to explain, wish I could attach a screenshot. I changed Firefox as my default browser, it works as default for some apps. But for some I have to select the always option. The ymgt ad popped up but on Chrome instead of Firefox. Please help!
July 6th, 2019Go to Android Settings > Apps > Chrome and locate Open by default option, click on it and then click CLEAR DEFAULTS button. This procedure might vary between different Android versions, but this is the gist of it.
July 6th, 2019I’ve installed Firefox and make it as default browser (disabled Chrome). What’s next? What else do I need to install?
July 12th, 2019Nothing, simply wait until another popup occurs and when prompted choose Firefox to open that url / link. Firefox will automatically log the information in the log file as explained in the article.
Then you have to manually open that log file with a text editor (or use File Manager to locate and open it) and see which application triggered the browser.
Please note that application id reported is in reverse domain format, so you have to figure it out what is the app’s Market name/title. It usually contains a known word, but in some cases it only holds parent company title.
July 12th, 2019great it helped
July 12th, 2019thanks
Ever since I installed the modified Firefox my browser stopped getting hijacked. I initially thought that maybe the application that was causing this might have been updated in the meantime and that maybe the developer removed the library that was causing it from his application. I uninstalled Firefox and then the problem started to manifest again. Is it possible that they are now checking if you have either Firefox installed as the default browser (I don’t know if they can also check it’s version) to see if they trigger the browser hijack in order to make it harder to detect the package of the app that’s causing this?
July 14th, 2019Not sure, maybe. Have you checked modified Firefox’s log file?
July 14th, 2019It didn’t create a log because not triggered it.
July 14th, 2019Well, I am not sure, really. Install it back and then wait, given the ‘randomness’ of event, sometimes you may need to wait 7-10 days, before it happens again. At one point, as I described in the article, I also thought it went away, but it occurred again after 7 days or so. Just be patient and if you catch it, please report it here. Thanks!
July 14th, 2019I have identified the application that was hijacking my browser. Thanks for help.
July 16th, 2019Great! Now just make sure to contact app developer, since their app is in danger of being permanently banned in the Play Store.
July 16th, 2019I had a chat with the developer. He is using ElephantData SDK in his app.
July 17th, 2019what is the name of this app?
July 17th, 2019It may be interesting to know particular title, however, given the time and scope of their operations, one can only assume that there are at least several hundreds, if not thousands, apps infected.
July 17th, 2019I followed the instructions and downloaded the Firefox app and set it as my default browser. I then waited until the ymgt page popped up via firefox but now I can’t find the log file anywhere. Using the standard “Files” app I go into internal storage and there is no root folder or log folder and no file called moz_url_log.txt. I then tried out some different file explorer apps and eventually came across a separate root folder but again there was no log folder and no sign of a file called moz_url_log.txt. Any idea how I can locate this log? Thanks
July 23rd, 2019Check in Android System Settings > Apps > Firefox app’s permissions and make sure writing / storage access is enabled. Also, use File Manager’s search function to find moz_url_log file.
July 23rd, 2019Hey just letting you know that going into the app permissions and enabling writing/storage access seems to have worked for me as it created a log and I could see an app that seemed to be bringing up the ygmt page. Having deleted that app I’ve had no problems since. Btw the app was “com.videocutter.mp3converter” listed on the app store as “Video to MP3 Converter, RINGTONE Maker, MP3 Cutter” made by AppSourceHub with a green icon. So if you have this app delete it! Many thanks for helping me with this I really appreciate it, it was driving me crazy!
August 6th, 2019Great! You can also contact developer (on Play Store’s app page scroll down under Developer contact section and click on Email or Website if available). I don’t think it is intentional, and Google may shut down their account and all apps once they find out.
August 6th, 2019Same as Mike,
July 24th, 2019I did allow permission for storage and using File manager but cannot find any log file. Please help…
Hi, I wanted to thank you so much for this guide that finally helped me solving this browser hijack problem that was cursing me since the last week. The custom Firefox app did the job. However setting it as default browser app was not sufficient because the offending app was still pushing its spam scheduled command through the Chrome browser.
July 28th, 2019So what I did was to disable temporarily the Chrome app and wait until the offending app opened up Firefox.
When it did so, Firefox produced the log file into the internal storage and I could read into it the name of the offending app.
This was an app that I installed through the Play Store more than 1 year ago and never created problems until a very recent update.
No famous anti malware app could find this out!
I notified Google and flagged the app which was APK Extractor Lite. Without you I would have never found a solution. Thanks!
You’re welcome. Glad you fixed it and thanks for the tip about Chrome, it will definitely help others.
July 28th, 2019Same as the two gentelman above. I’ve just installed the Mozilla app, spam haven’t appeared yet, but Firefox doesn’t create any log file!
Please let us know if you have any suggestions or ideas :)
Thanks,
July 29th, 2019Tom
Hi Tom, please read comments and replies above for possible solutions, try to disable Chrome browser app (temporarily) and make sure Firefox app has storage write permissions.
July 29th, 2019Already done that. Didn’t help. I still don’t have a log file.
July 29th, 2019Hi Tom, I am really out of ideas why it doesn’t work. Could be a problem with compatibility of Firefox app and specific Android versions and devices. Out of curiosity, can you specify your device and Android OS version?
July 29th, 2019I have the same issue with ymgt, It was the powervpn
August 8th, 2019Custom Firefox is not working. What do you recommend? It takes forever to install and once installed, it opens up to a crashed page. I am able to restart it and the crashed page is not shown. However, when I go to Gmail and open up a link and specify Firefox as the always default browser, it always opens up a crashed page. I uninstalled and installed the app, but that doesn’t help.
To be clear this is a custom version of Firefox, and so any Firefox won’t do, correct? I see that this is version 65.0.1 and the one I had before that I had to uninstall to be able to install this one was version 66.00.
My phone is a Samsung Galaxy S5 running Android 5.0.
About 3 to 4 weeks ago my phone started opening up .xyz pages on the Samsung Internet Browser. It now seems to do it less often after I cleared the cache and deleted the data for that browser, but when I leave the phone untouched for several hours and then unlock it, the first thing it does is open up my browser to .xyz pages. Very annoying! I can’t wait to find out which app is doing this. I have looked into all the other supposed solutions (apps with no name, clearing cache and data of the browser, etc.), but none of them apply to me.
I really hope a solution can be offered as I don’t want to do a Factory Reset of my phone over this.
Thanks.
August 27th, 2019Hi, sorry, but I have no idea why the app is not working on your device. Your best chance is to try and report this in Kaspersky’s forum and see if they plan to release another modified Firefox app that might work for you.
In the meantime, if you remember which apps you updated or installed in the recent month, as you say, try uninstalling or disabling them one by one, and see if you can catch the culprit that way. Yes, I know, it is not convenient, but the key issue here is that you have installed some infected app or updated to infected version; downgrade can be another sort of fix.
Don’t bother removing apps from big companies and brands like Facebook, Twitter, Instagram, Snapchat, Google, YouTube etc. Those are not the culprits in this case. It has to be an app (game or utility) from a smaller company or independent developer.
No factory reset is required! Don’t do that.
August 27th, 2019Thank you very much for the prompt response and I am very sorry for the late response.
I did think about looking at recent things installed, but when I went to the Play Store and looked at installed apps and Sorted them by Last Updated, I didn’t see anything odd or from a not too famous company for the month of August and even July. Using ES File Explorer and sorting by Modified Date, it for some reason shows me some extra apps. It showed two scanner apps as being modified in August, though they weren’t updated. I uninstalled those two, but that didn’t help. I even uninstalled most of the other apps from August from famous to relatively famous brands, but that also didn’t help.
I feel like all of this started one day when I was browsing some sites and some things popped up asking for O.K. to be clicked on and I just clicked O.K. instead of closing the tab (I think I couldn’t close the tab; don’t remember). However, clearing cache and data for the browser hasn’t solved the problem, so either that wasn’t the cause or an app or widget or something got installed.
Anyhow, I am so upset about this and want to catch the culprit so bad. I also thought this used to happen only when I would unlock the phone after x number of minutes or hours, but it’s now happening when I am using the phone after x number of minutes or hours. The last time while on the road using the GPS, it took me away from that screen to the browser to show me a random page with a .xyz domain! It’s so annoying and infuriating!
The link that you have posted for the Kaspersky forum says that that forum is closed and they are not allowing new posts to be created. They do however provide a link to the new forum. I created a topic there about this (not sure if I posted it in the right category though) and I truly hope someone can provide some help.
You can view the post here:
September 7th, 2019community.kaspersky.com/kaspersky-internet-security-13/custom-firefox-with-logging-capabilites-for-android-does-not-work-in-android-5-0-lollipop-mozilla-apk-3328
Any ideas how to disable Samsung Internet browser so these links open in the modified Firefox instead? I’ve disabled Chrome completely and set the phone’s settings to default to Firefox. But the links still open in the Samsung Internet browser without any way to disable that app.
September 11th, 2019Try opening Settings > Apps > Internet (or whatever your Samsung Browser app’s name is), click on it and there should be a Disable button.
September 11th, 2019I did try that. Unfortunately while I can set another browser as Default, this built-in app won’t allow you to click the Disable button.
September 11th, 2019Is there a “clear defaults” option, as well? You can try that instead. Otherwise, only if you root the phone you’ll be able to remove it. Or you can uninstall apps one by one, until you find the culprit. Last resort is factory reset, but I think you can avoid that, as mentioned in one of the comments above.
September 11th, 2019I never did get the Firefox default to work. However, after some sleuthing I did find similar stories to mine that stated the pre-installed “Peel Remote” app was the problem. I was getting these xyz pages easily 10 times per day. Since late Wednesday when I removed Peel Remote it hasn’t happened again. Oddly enough, that app cannot be found in the Google Play Store to report it as malicious. Thanks for this post and your assistance. Glad to have this ended.
September 14th, 2019I tried Macafe and Nox security for this issue, but no use.. after read your blog, finally I uninstalled sci-fi calculator & some more apps. But I think calculator is the culprit.. now I observed 1 full day . As of now no issue. ( not tried Kaspersky or any other scanner ) txs for support
March 16th, 2020