WHAT IS CIDRAM?
CIDRAM (Classless Inter-Domain Routing Access Manager) is a simple IP range filter written in PHP programming language and intended to be used as a wrapper for any PHP file on your web server. Normally, it is intended to be used as a main layer sitting on top of your CMS (Content Management System) such as WordPress, Drupal, Joomla, phpBB, vBulletin etc. There are countless CMSs out there written in PHP that could greatly benefit from it.
At the time of this writing it is still in the early stage of development, so it’s features and functionalities will probably change over time. The basic conceptual idea behind it was inspired by ZB Block protection script, however, with few notable advantages: IPv6 CIDR support, streamlined code & actively maintained GitHub repository, improvements in terms of performance/optimization and organization of it’s key components.
CIDRAM INSTALLATION
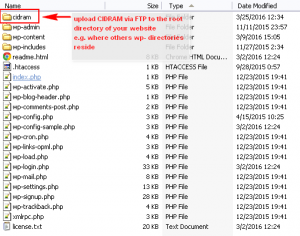
It could not be simpler, really. Since the logic/philosophy of including files was covered in ZB Block tutorial already, we will not waste our time here explaining all the details. All you have to do is download latest CIDRAM .zip package, upload it via FTP server into your public_html or www directory, include a php call to the CIDRAM’s loader.php file and you are essentially done.
But, wait, in which file should I make the call to CIDRAM’s loader.php? Usually, this is the “loader” file itself of a particular CMS. In case of WordPress CMS, it is located in the root of every WP installation and it is named wp-load.php. Other CMS systems might have a different loading sequence, or, if you do not use a CMS system at all, you have to put this call in every stand-alone .php file (or common include) that you wish to protect with CIDRAM filter.
CIDRAM IMPLEMENTATION @ WordPress Example
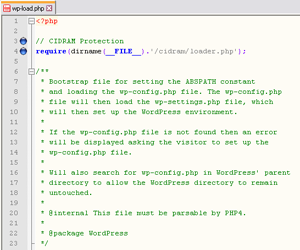
Simply, open wp-load.php file (preferably with a dedicated code editor such as Notepad++, or ordinary Notepad plain-text editor as a last resort – do not use OpenOffice, Microsoft Word and similar tools!), then locate the first line <?php (this is opening PHP tag), and immediately afterwards add below code:
// CIDRAM
require(dirname(__FILE__).'/cidram/loader.php');
SAVE & DONE!
<IfModule mod_php*.c>
php_value auto_prepend_file /relative/path/to/cidram/loader.php
</IfModule>where * is usually PHP version and relative path is something along these lines:
[1] /var/www/mywebsite.com/cidram/loader.php
[2] /home/user_name/public_html/cidram/loader.php
[3] root/mywebsite.com/htdocs/cidram/loader.php
However, there are several conditions that needs to be met in order for the above command to work:
1) This method requires Apache configured to use PHP as a module (mod_php), otherwise you will need a PECL module for htaccess support in FCGI/FastCGI setups.
2) This method requires root access to php.ini configuration file or – at least – enabled support for outside .ini directives overrides (outside ini overrides could be a security threat, though).
3) Auto-Prepend function allows to include one and only one PHP file for execution. In order to execute multiple chained files (for example, if you use more than one protection script), you will have to combine them all within a single .php file, using include_once() or require_once() PHP functions.
WHAT’S THE DIFFERENCE?
include()/include_once() are error-friendly, if the file is not found, PHP will still execute the rest of the things, while require()/require_once() will throw fatal error if the file is not found or inaccessible.
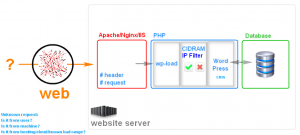
HOW CIDRAM WORKS?
Here is a basic block diagram where CIDRAM is executed inside the PHP chain (example given for WordPress):
Every time you access your WordPress-powered website, PHP will initialize it through wp-load.php sequence and the very first thing that will be executed is CIDRAM. CIDRAM will then analyze the traffic, namely header of the incoming request and if the IP address matches one of the ranges in the .dat tables, it will be blocked! On the other hand, if the IP does not belong to the predefined rules, PHP will continue to execute WordPress and the request will be served.
CIDRAM VAULT DIRECTORY
This directory has the same purpose as ZB Block protection script. It holds some key components for the script proper operation, and you should restrict access to all of the files in here (preferably with 0700 for maximum flexibility and security).
config.ini
This is a standard configuration initialization file, and it is pretty much self-explanatory. After you finish with implementation, you should open this file and customize some parameters, including logging, forwarded IP address header field, optional contact email address (in case of false positives, but use separate email account, since you are probably going to receive huge amount of SPAM!), and finally, rules that you wish to apply:
- Generic/Standard rules
- Cloud/Hosting services
- Bogon ranges
- known SPAM ranges
As CIDRAM is still in heavy development, the available options will be most probably modified and expanded over time.
ipv4.dat, ipv6.dat
These files store the key IP Address ranges information by which it makes the allow/deny decisions. All IP Addresses are written in CIDR notation (naturally), regardless of the fact weather they belong to IPv4 or IPv6 standard. You can, of course, restrict a single IP Address simply by using the appropriate mask at the end (e.g. /32 for IPv4 and /128 for IPv6), but – remember, you must put it in CIDR format!
ipv4_custom.dat, ipv6_custom.dat
You can specify your own custom IPv4 and IPv6 ranges here, separated from the mainline official rules.
template.html
This is a HTML template file that is shown to the visitors when they trigger any access deny rule. It comes with some basic inline CSS style.
template_custom.html
This is a bare-bone HTML template file provided for your convenience and further customization. Remember, you need to copy/replace original template.html file to see the results.
/lang subdirectory
Hold translations for several world languages, and you can translate into your own. Nice touch! :)
This is all there is to it, really. All other files there are internal/specific that users shouldn’t modify under normal conditions.
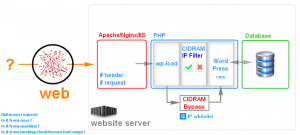
HOW TO COMPLETELY BYPASS CIDRAM FOR SPECIAL IP ADDRESS WHITE LIST?
This is exactly the same principle we’ve used in ZB Block, but adapted to work with CIDRAM. In case you have specific issues with CIDRAM that you do not know how to solve, or simply wish to completely bypass it for special white-listed IP ranges, you can do it in the following way.
Here is a block-diagram that illustrates our bypass:
1) First, create loaderwrapper.php empty file inside CIDRAM main directory (along with original loader.php in there).
2) Inside CIDRAM /vault directory create ipwldb.csv file and place white-listed IPs in comma-separated fashion (or copy this file from ZB-Block /vault directory), for example:
::1,127.0.0.1,192.168.0.1
3) Copy/Paste this code into loaderwrapper.php file:
<?php
// CIDRAM White List Bypass
// Ensures full override of CIDRAM white listed IP Addresses
$whiteList = dirname(__FILE__) . '/vault/ipwldb.csv'; // White List Database
if (file_exists($whiteList)) {
$whiteListContent = @file_get_contents($whiteList); // load White List content
$whiteListContent = str_replace(' ', '', $whiteListContent); // remove white space
$whiteListContent = rtrim($whiteListContent, ','); // remove last comma
$whiteListContentArray = explode(',', $whiteListContent); // explode array by comma
$userAccessIPAddress = $_SERVER['REMOTE_ADDR']; // get access IP address
if ( !in_array($userAccessIPAddress, $whiteListContentArray) ) {
// call CIDRAM
require(dirname(__FILE__).'/'.'loader.php');
}
} else {
// call CIDRAM (safety fallback)
require(dirname(__FILE__).'/'.'loader.php');
}
?>
4) Open wp-load.php and replace the original line that calls loader.php with the newly created file loaderwrapper.php:
// CIDRAM
require(dirname(__FILE__).’/cidram/loaderwrapper.php’);
Now CIDRAM will be completely bypassed for trusted IPs and your WordPress administration work will be uninterrupted as if it was never installed in the first place, but it will keep the protection ON for everyone else!
CONCLUSION
Key question: Is CIDRAM going to replace ZB Block? Well, at the present time no, not exactly. ZB Block offers additional features for the time being (despite the lack of IPv6 support), such as filtering based on referrer and User Agent. If those features gets incorporated over time, then the answer will be – yes, without a doubt. For now, you need to use both tools in layered stack (call first whichever you prefer), and they will function in harmony.










![Xiaomi App - How To Re-Install Stock Factory Version - How To Fix Corrupted Gallery App [no root]](https://tehnoblog.org/wp-content/uploads/2025/09/Xiaomi-Gallery-App-Code-Bugs-Artwork-1024x576.png)















5 Comments
Add Your CommentHOW TO COMPLETELY BYPASS CIDRAM FOR SPECIAL IP ADDRESS WHITE LIST?
Just what I needed. Thank you for posting the solution.
April 16th, 2018You’re welcome! I’ve just updated the code with 2 extra lines, a small safety fallback in case you accidentally (or on purpose) delete the ipwldb.csv file (not very likely, but just in case, maybe during CIDRAM automated update or something).
Also, you can call the whitelisted .csv file name whatever you want, as long as you later reference it properly in the code:
$whiteList = dirname(__FILE__) . '/vault/ipwldb.csv';Regards
April 17th, 2018::1,127.0.0.1,192.168.0.1 doesn’t make sense to me since I’m not tech savvy. Why can’t I just google my IP and paste and copy it and use that?
I hate that CIDRAM is blocking me today for whatever reason but I can’t figure out why since… well… I keep getting blocked!
September 18th, 2018Hi, check your log in CIDRAM, it should give you a clue. You can add your IP to whitelist, but it may change depending on your ISP, company, etc.
Addresses you mentioned are local, and should never be blocked.
September 18th, 2018Nice article, just what I was looking for, I think. I just installed CIDRAM three days ago and today I noticed that it was blocking (I think) a lot of wp-cron updating actions as judging from the url. Anyway I just wanted to add that instead of adding the code in step #4 into the wp-load.php file, I added it into a child-theme’s functions.php file and it seems to have worked. At least it didn’t break anything. I will check in a day or so and see if it still blocks the domain in use.
May 28th, 2020